Anyone trying to install MS Office either 2007 or 2010??? And do you have the Panda Cloud Antivirus running?
Well, there have been instances reported of installation error 1935 and a rollback of the install.....
Here's the fix....completely uninstall Panda Cloud antivirus and restart the computer....then
install Office....restart the computer....then reinstall Panda Cloud antivirus......
Just another glitch in technology....not every program is happy with each other...arghh!
HELPING THE ONLINE COMMUNITY GAIN A KNOWLEDGE OF SIMPLE TASKS USING THEIR DEVICES
Sunday, May 30, 2010
Homegroup Troubles? Pretty common....read on for answer..
Hey gang, if you are having trouble connecting all your PC's together with the Homegroup situation and Windows 7 here's a quick fix.....change the Homegroup password on the first PC....and then when you go to the Homegroup button in the control panel it will say "Homegroup changed the password"..duh......you type in the new one it generated and wowwee...yer hooked up again....amazin' technology......this winders stuff....
Friday, May 28, 2010
Desktop Wallpapers...great site to get 'em at
Found this site and the cool thing about it is when you click on a wallpaper you like it will
auto adjust based on your monitor display size...pretty cool huh?
Then if you like it......right click on the wallpaper>"set as desktop background" and viola...it's yours!
Here's the LINK
auto adjust based on your monitor display size...pretty cool huh?
Then if you like it......right click on the wallpaper>"set as desktop background" and viola...it's yours!
Here's the LINK
Thursday, May 27, 2010
How to test your graphics....get Furmarks....
Sometimes the graphics on your computer will act up and you can't figure out what happened....
well, with this program you can run it through the cogs and see what is going on...that is,
if it is still operable....in other words "a stress test"
get FURMARKS HERE for Win Xp and Vista 32 Bit and Win 7
well, with this program you can run it through the cogs and see what is going on...that is,
if it is still operable....in other words "a stress test"
get FURMARKS HERE for Win Xp and Vista 32 Bit and Win 7
Monday, May 24, 2010
How to use the Microsoft Malicious Software Tool
Yes, you downloaded it and all that but now where is it and how do you use it?
Read on:
How to Run the Malicious Software Removal Tool Manually
Follow the steps below to open MSRT and change the default settings.
1) Click on Start, Run
2) Type MRT and Press Enter
3) You'll be presented with the following screen, click on the Next button

4) Normally, the removal tool runs the Quick Scan, but for more thorough results, choose FULL SCAN and click Next

5) Now the Malicious Software Removal Tool will scan your entire hard drive for infections and problems.

6) Once the scan is completed, you should see the following screen if your computer is free of infection.

Read on:
How to Run the Malicious Software Removal Tool Manually
Follow the steps below to open MSRT and change the default settings.
1) Click on Start, Run
2) Type MRT and Press Enter
3) You'll be presented with the following screen, click on the Next button
4) Normally, the removal tool runs the Quick Scan, but for more thorough results, choose FULL SCAN and click Next
5) Now the Malicious Software Removal Tool will scan your entire hard drive for infections and problems.
6) Once the scan is completed, you should see the following screen if your computer is free of infection.
Rogue Viruses pose as safe programs...beware
The latest down the net pike.....these programs pose as harmless and the links are appealing to get you to download and try them...DON"T DO IT!
Not unless you want us techs to fix your computer cuz its crashed!
One of them is "Antispyware 2010" another is "Personal Security"...plus bunches and bunches more.....
Once you get 'em they pretty much disable all the programs from starting so you can't do anything...arghh!
FROM PC WORLD....READ ON.....
Not unless you want us techs to fix your computer cuz its crashed!
One of them is "Antispyware 2010" another is "Personal Security"...plus bunches and bunches more.....
Once you get 'em they pretty much disable all the programs from starting so you can't do anything...arghh!
FROM PC WORLD....READ ON.....
Because of Google's large market share in the Internet search engine business, hackers developed a vested interest in ensuring that their attacks are effective in poisoning Google results, according to software company Symantec.
 "Google's breadth and speed of indexing also play a role," added Symantec, a company involved in providing security, storage and systems management solutions.
"Google's breadth and speed of indexing also play a role," added Symantec, a company involved in providing security, storage and systems management solutions.
Symantec reported that search engine results poisoned with links to fake antivirus software have been a constant problem for Internet users. However, it is an effective way for cyber attackers to infect users' machines.
Based on Symantec's report on "Rogue Security Software" -- the culprits of these "toxic" search results are typically scam perpetrators who use a range of black hat search engine optimization (SEO) techniques to poison search engine results and increase the ranking of their scam websites on search engine indexes. A rogue security software program is a misleading application that pretends to be legitimate security software, but provides the user with little or no protection. In some cases, it actually facilitates the installation of malicious code that it claims to protect against.
Symantec has observed search results constantly and generated statistics on the top search trends every hour and determined how many were malicious (within the first 70 Google search results).
Among the key findings identified between March to April 2010, on Google search results include the following:
• On average at any given hour, 3 out of the top 10 search trends contained at least one malicious URL within the first 70 results;
• On average, 15 links out of the first 70 results were malicious for search terms that were found to be poisoned (had at least one malicious URL);
• On average on any given day, 7.3% of links are malicious in the top 70 results for top search terms (see Figure 1);
• The most poisoned search term resulted in 68% of links leading to malicious pages in the first 70 results;
• Almost all of the malicious URLs redirect to a fake antivirus page.
It is apparent that attackers continue to be effective at poisoning search results. They have an automated infrastructure that is able to automatically collect the latest, most popular search trends and poison the results, the company said.
Symantec advises netizens to be careful when clicking on search result links, especially when searching for hot search topics. The company also advised to follow its Twitter feed to find out the latest news on Internet threats.
Symantec reported that search engine results poisoned with links to fake antivirus software have been a constant problem for Internet users. However, it is an effective way for cyber attackers to infect users' machines.
Based on Symantec's report on "Rogue Security Software" -- the culprits of these "toxic" search results are typically scam perpetrators who use a range of black hat search engine optimization (SEO) techniques to poison search engine results and increase the ranking of their scam websites on search engine indexes. A rogue security software program is a misleading application that pretends to be legitimate security software, but provides the user with little or no protection. In some cases, it actually facilitates the installation of malicious code that it claims to protect against.
Symantec has observed search results constantly and generated statistics on the top search trends every hour and determined how many were malicious (within the first 70 Google search results).
Among the key findings identified between March to April 2010, on Google search results include the following:
• On average at any given hour, 3 out of the top 10 search trends contained at least one malicious URL within the first 70 results;
• On average, 15 links out of the first 70 results were malicious for search terms that were found to be poisoned (had at least one malicious URL);
• On average on any given day, 7.3% of links are malicious in the top 70 results for top search terms (see Figure 1);
• The most poisoned search term resulted in 68% of links leading to malicious pages in the first 70 results;
• Almost all of the malicious URLs redirect to a fake antivirus page.
It is apparent that attackers continue to be effective at poisoning search results. They have an automated infrastructure that is able to automatically collect the latest, most popular search trends and poison the results, the company said.
Symantec advises netizens to be careful when clicking on search result links, especially when searching for hot search topics. The company also advised to follow its Twitter feed to find out the latest news on Internet threats.
Lookout Mobile Security-Great App for your phone
Got Mobile Phone?
Well, help protect it with Lookout Software: Here is the scoop from
their page:
Mobile devices are a valuable target. The mobile device has become the most personal computer. Mobile devices contain personal information, access sensitive networks, and are now utilized for financial transactions. Lookout keeps your device safe and secure.
As with PCs, mobile devices are subject to viruses, malware, and hackers. Mobile devices have quickly evolved from phones to fully functional mobile computers enabling web browsing, multimedia, advanced communication.
Downloading applications, accessing public Wi-Fi hotspots, and use of Bluetooth are all commonplace and targeted by attackers.
Download the App HERE
Stay safe in the Web World gang!
Well, help protect it with Lookout Software: Here is the scoop from
their page:
Mobile devices are a valuable target. The mobile device has become the most personal computer. Mobile devices contain personal information, access sensitive networks, and are now utilized for financial transactions. Lookout keeps your device safe and secure.
As with PCs, mobile devices are subject to viruses, malware, and hackers. Mobile devices have quickly evolved from phones to fully functional mobile computers enabling web browsing, multimedia, advanced communication.
Downloading applications, accessing public Wi-Fi hotspots, and use of Bluetooth are all commonplace and targeted by attackers.
Download the App HERE
Stay safe in the Web World gang!
Saturday, May 22, 2010
Google Password Decryptor
GooglePasswordDecryptor is a tool to instantly recover Google account passwords stored by various Google applications as well as popular web browsers...
A handy tool to keep around in case you need it...and its portable...just download the zip file and unzip it onto a USB drive...(which is what I recommend for portable programs anyhow
Get it HERE
A handy tool to keep around in case you need it...and its portable...just download the zip file and unzip it onto a USB drive...(which is what I recommend for portable programs anyhow
Get it HERE
Best Free Screen Capture Program Out There
I recommend FastStone Screen Capture-portable version....just download the zip file....extract it and click on the little bright icon to
start the program...it works on Windows 7 too! The snipping tool with Win 7 is goofy...you draw with your mouse around the screen....pretty lame if you ask me....this little nifty deal gives you the option to capture the whole screen or just crop what you want.....
get it HERE and go with it.....you will wish you had gotten it before now!
start the program...it works on Windows 7 too! The snipping tool with Win 7 is goofy...you draw with your mouse around the screen....pretty lame if you ask me....this little nifty deal gives you the option to capture the whole screen or just crop what you want.....
get it HERE and go with it.....you will wish you had gotten it before now!
Friday, May 21, 2010
What is a Trojan? Here's the answer....
A Trojan, sometimes referred to as a Trojan horse, is non-self-replicating malware that appears to perform a desirable function for the user but instead facilitates unauthorized access to the user's computer system. The term is derived from the Trojan Horse story in Greek mythology.
Operations that could be performed by a hacker on a target computer system include:
A trojan differs from a virus in that only a file specifically designed to carry it can do so. Installation and distribution
Trojan horses can be installed through the following methods:
(Posted courtesy of Wikipedia)
Purpose and operation
Trojan horses are designed to allow a hacker remote access to a target computer system. Once a Trojan horse has been installed on a target computer system, it is possible for a hacker to access it remotely and perform various operations. The operations that a hacker can perform are limited by user privileges on the target computer system and the design of the Trojan horse.Operations that could be performed by a hacker on a target computer system include:
- Use of the machine as part of a botnet (i.e. to perform spamming or to perform Distributed Denial-of-service (DDoS) attacks)
- Data theft (e.g. passwords, credit card information, etc.)
- Installation of software (including other malware)
- Downloading or uploading of files
- Modification or deletion of files
- Keystroke logging
- Viewing the user's screen
- Wasting computer storage space
- Crashing the computer
A trojan differs from a virus in that only a file specifically designed to carry it can do so. Installation and distribution
Trojan horses can be installed through the following methods:
- Software downloads (e.g., a Trojan horse included as part of a software application downloaded from a file sharing network)
- Websites containing executable content (e.g., a Trojan horse in the form of an ActiveX control)
- Email attachments
- Application exploits (e.g., flaws in a web browser, media player, messaging client, or other software that can be exploited to allow installation of a Trojan horse)
Removal
Antivirus software is designed to detect and delete Trojan horses, as well as preventing them from ever being installed. Although it is possible to remove a Trojan horse manually, it requires a full understanding of how that particular Trojan horse operates. In addition, if a Trojan horse has possibly been used by a hacker to access a computer system, it will be difficult to know what damage has been done and what other problems have been introduced. In situations where the security of the computer system is critical, it is advisable to simply erase all data from the hard disk and reinstall the operating system and required software.Current use
Due to the growing popularity of botnets among hackers, Trojan horses are becoming more common. According to a survey conducted by BitDefender from January to June 2009, "Trojan-type malware is on the rise, accounting for 83-percent of the global malware detected in the world".[2](Posted courtesy of Wikipedia)
Google to offer encrypted browsing....here's how...
People who want to shield their use of Google's Web search engine from network snoops now have the option of encrypting the session with SSL protection.
SSL (Secure Sockets Layer) technology is designed to prevent unauthorized parties from sniffing data traveling between a user's computer and a server.
In the case of Google search, SSL will protect the transmission of search queries entered by users and the search results returned by Google servers.
Google will begin rolling out the encrypted version of its Web search engine on Friday. It will be available by typing "https" instead of "http" in the URL address bar.
"We think users will appreciate this new option for searching. It's a helpful addition to users' online privacy and security, and we'll continue to add encryption support for more search offerings," wrote Evan Roseman, a Google software engineer, in an official blog post.
The SSL Web search will be in beta, or test, mode for now and the user experience will vary from the regular service in a few ways. For instance, it will likely be slower because a secure connection has to be established. Initially, the SSL option will be available only for Web search and will not cover Google's specialty engines like image and maps search.
Google offers SSL protection for other of its services, like Gmail and the hosted Docs office productivity suite.
SSL (Secure Sockets Layer) technology is designed to prevent unauthorized parties from sniffing data traveling between a user's computer and a server.
In the case of Google search, SSL will protect the transmission of search queries entered by users and the search results returned by Google servers.
Google will begin rolling out the encrypted version of its Web search engine on Friday. It will be available by typing "https" instead of "http" in the URL address bar.
"We think users will appreciate this new option for searching. It's a helpful addition to users' online privacy and security, and we'll continue to add encryption support for more search offerings," wrote Evan Roseman, a Google software engineer, in an official blog post.
The SSL Web search will be in beta, or test, mode for now and the user experience will vary from the regular service in a few ways. For instance, it will likely be slower because a secure connection has to be established. Initially, the SSL option will be available only for Web search and will not cover Google's specialty engines like image and maps search.
Google offers SSL protection for other of its services, like Gmail and the hosted Docs office productivity suite.
Thursday, May 20, 2010
Create free cards or anything with this!
Do you want to make a card, recipe, flyer etc.
and don't have the software to do it?
Well then, here is the answer......HP Creative Studio....
Just click HERE and get creative!
and don't have the software to do it?
Well then, here is the answer......HP Creative Studio....
Just click HERE and get creative!
Tuesday, May 18, 2010
What is Greasemonkey again? Here's the answer....
To put it simply....it blocks (or allows) certain parts of websites....and that's basically all you need to know at this point because the main reason I recommend it is Facebook with all those ads....yikes....so install it and run it and settle back for breezy web surfin'...and safely....you can download more scripts (which cause the webpages you are viewing to be more functional) Get SCRIPTS
Get Greasemonkey HERE for Firefox
Get Greasemonkey HERE for Firefox
Facebook privacy...keep yourself protected from prying eyes
With all the buzz now about Facebook privacy concerns here is a little open source app that will help you see what is going on while you are browsing your facebook page.....read below courtesy of ReclaimPrivacy.org.....
Get Informed
Keep up with the latest news about privacy policies on Facebook.- The Erosion of Facebook Privacy eff.org
- Facebook Privacy Changes eff.org
- 7 Things to Stop Doing Now on Facebook yahoo.com
- Facebook's Gone Rogue wired.com
Get Protected
This website provides an independent and open tool for scanning your Facebook privacy settings. The source code and its development will always remain open and transparent.- Drag this link to your web browser bookmarks bar: Scan for Privacy
- Log in to facebook.com and then click that bookmark
- You will see a series of privacy scans that inspect your privacy settings and warn you about settings that might be unexpectedly public.
- Follow us on Facebook to hear about the latest updates.
Sunday, May 16, 2010
DropBox.....set it up and drag and drop files....
What is it? Well, it is a kind of cyber file system where you can have your own "storage bin" so to speak and drag your files in there and then can access them from any computer, anywhere by just logging into DropBox on the Net....
Get it HERE
Info :
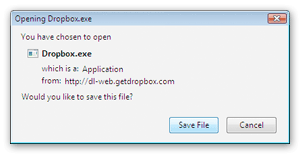
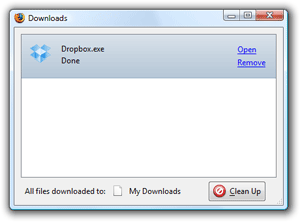
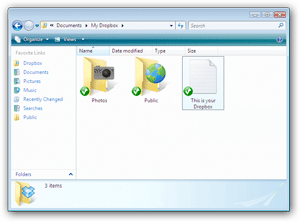
Get it HERE
Info :
How to Install Dropbox

1. Save the Dropbox application

2. Run the Dropbox Installer
From your browser's Downloads window, click 'Open' to start the installer
3. After this, you should be good to go!
Need any more info? Check out our tour or help sections.Saturday, May 15, 2010
Google Wireless Blunder.....whoops.....
For those of you who have "unsecured" routers in your homes....now is the time to get that fixed! And if you don't know how call one of your tech friends who can get it going for you....here's what Googles "street view" did this week....read on....
"Don't be evil" has gone all 1984 on us. Or so it seems after Google revealed Friday that its Street View cars, in addition to snapping photos of the world's roadways, have also been collecting sensitive personal information from unencrypted wireless networks.
It was no secret that Google's cars had already been collecting publicly broadcast SSID information (Wi-Fi network names) and MAC addresses (unique numbers for devices like Wi-Fi routers). But this techie data, which is used for location-based services such as Google Maps, didn't include any "payload data," or personal information sent over the network.
Or so "Big Brother" Google claimed on April 27. But yesterday the search behemoth 'fessed up to a security gaffe of Orwellian proportions. Due to a piece of code written in 2006 by an engineer for an experimental Wi-Fi project, Google had in fact been collecting those private bits after all:
"But it's now clear that we have been mistakenly collecting samples of payload data from open (i.e. non-password-protected) WiFi networks, even though we never used that data in any Google products," wrote Alan Eustace, Google senior VP, engineering & research.
Wow. That's freaky and strange. And not in a good way, either.
Google was smart to open up about the spying incident. An attempted cover-up would have proven disastrous, particularly when numerous consumer and government agencies worldwide have criticized the search company's seemingly insatiable appetite for personal information, a quest that critics say infringes on individual privacy rights.
There's little doubt the Wi-Fi spying incident won't fade away quietly. In fact, the Electronic Frontiers Association (EFA) and Australia Privacy Foundation (APF) have joined forces to question potential security mishaps by Google's Street View, according to a report by Computerworld-Australia.
The latest Street View controversy is sweet fodder for conspiracy theorists. As someone said to me responding to the news: "Imagine, Google driving around in vans, taking pictures of EVERYTHING, and gobbling up Wi-Fi signals like some new-age techno CIA." Sweet conspiracy fodder - indeed.
If nothing else, Google's security gaffe should serve as a wake-up call to clueless folk who've yet to encrypt their home Wi-Fi networks. Do you get it now? Anybody may be snooping on you."
"Don't be evil" has gone all 1984 on us. Or so it seems after Google revealed Friday that its Street View cars, in addition to snapping photos of the world's roadways, have also been collecting sensitive personal information from unencrypted wireless networks.
It was no secret that Google's cars had already been collecting publicly broadcast SSID information (Wi-Fi network names) and MAC addresses (unique numbers for devices like Wi-Fi routers). But this techie data, which is used for location-based services such as Google Maps, didn't include any "payload data," or personal information sent over the network.
Or so "Big Brother" Google claimed on April 27. But yesterday the search behemoth 'fessed up to a security gaffe of Orwellian proportions. Due to a piece of code written in 2006 by an engineer for an experimental Wi-Fi project, Google had in fact been collecting those private bits after all:
"But it's now clear that we have been mistakenly collecting samples of payload data from open (i.e. non-password-protected) WiFi networks, even though we never used that data in any Google products," wrote Alan Eustace, Google senior VP, engineering & research.
Wow. That's freaky and strange. And not in a good way, either.
Google was smart to open up about the spying incident. An attempted cover-up would have proven disastrous, particularly when numerous consumer and government agencies worldwide have criticized the search company's seemingly insatiable appetite for personal information, a quest that critics say infringes on individual privacy rights.
There's little doubt the Wi-Fi spying incident won't fade away quietly. In fact, the Electronic Frontiers Association (EFA) and Australia Privacy Foundation (APF) have joined forces to question potential security mishaps by Google's Street View, according to a report by Computerworld-Australia.
The latest Street View controversy is sweet fodder for conspiracy theorists. As someone said to me responding to the news: "Imagine, Google driving around in vans, taking pictures of EVERYTHING, and gobbling up Wi-Fi signals like some new-age techno CIA." Sweet conspiracy fodder - indeed.
If nothing else, Google's security gaffe should serve as a wake-up call to clueless folk who've yet to encrypt their home Wi-Fi networks. Do you get it now? Anybody may be snooping on you."
Thanks to
Jeff Bertolucci, PC World
GMail Backup......recommend you do it....
Do you trust Google to never fail? Well, we all know that bad things happen to good technology...right?
So get this program.....run it and backup your Gmail items to a folder on your hard drive.....then you'll know it's not only out there "in the cloud"...but also in your little ole' computer hard drive or a USB flash drive is even better!
GMail Backup HERE
So get this program.....run it and backup your Gmail items to a folder on your hard drive.....then you'll know it's not only out there "in the cloud"...but also in your little ole' computer hard drive or a USB flash drive is even better!
GMail Backup HERE
Hotmail Versus GMail....next week's showdown!
All-new Hotmail to take on Gmail next Monday — On Monday, Microsoft will unleash a new version of its category-leading Hotmail email service that carries the fight against Google onto the screens of the hundreds of millions of lone users and small teams who swear by Gmail.
Watch for it........the competition is on!
Watch for it........the competition is on!
Friday, May 14, 2010
Google Docs.....try it!
The office war is on between Google and Microsoft....but if you want to have basic office features and for free just use the Docs in your Gmail account....in case you haven't noticed up above your gmail inbox you will see the links and one of them is ....duh....DOCUMENTS.....here you can create, view, send and everything else Word and Excel (MS) documents etc. etc....plus store them "in the cloud" for viewing wherever you are in the world via web browser and signing into your Google account....pretty neat huh?
Especially considering you get an automatic 7 gigs of space when you set up a Google account....check it out today!
Especially considering you get an automatic 7 gigs of space when you set up a Google account....check it out today!
Wednesday, May 12, 2010
Peppermint Linux now available!
What is it?
The latest installation of Linux OS.....a lighter, faster cloud based
operating system.....fast boot up and spin down times.....
Download HERE
Burn the .ISO file with IMGBURN.....and try it in your computer....remember to set your bios to boot from the CD.....that means before it starts up you put the CD in and hit "enter" continually as the computer is starting....hopefully it is set by default to boot from CD and not the hard drive.....
The latest installation of Linux OS.....a lighter, faster cloud based
operating system.....fast boot up and spin down times.....
Download HERE
Burn the .ISO file with IMGBURN.....and try it in your computer....remember to set your bios to boot from the CD.....that means before it starts up you put the CD in and hit "enter" continually as the computer is starting....hopefully it is set by default to boot from CD and not the hard drive.....
Friday, May 7, 2010
System File Checker- What Is it?
As most of you know by now files can get corrupted in the operating system and cause real havoc....
well, a simple checker is within the system and here's how to run it
go to "start"
and "run"
and then type in sfc /scannow
exactly as it is written.....this is windows system file checker and it will run through and make sure all the files
are in their proper position.....if not, it will tell you to put in your windows install disc and it will copy the files needed off of it....
well, a simple checker is within the system and here's how to run it
go to "start"
and "run"
and then type in sfc /scannow
exactly as it is written.....this is windows system file checker and it will run through and make sure all the files
are in their proper position.....if not, it will tell you to put in your windows install disc and it will copy the files needed off of it....
Thursday, May 6, 2010
Grooveshark-Awesome Online Free Listening!
Listen to whatever is out there in the web world .....stream music right to your computer.....ahhhh.....enjoy!
Here's the link
Here's the link
Monday, May 3, 2010
Windows 7 won't print!
Well, sure it will---you just have to go to "start" > "devices and printers" and you will see your printer there.....right click on the one you have installed---or the one you wish to use and hit "set as default"....then when you go to print something it will default to that one....
or the program you are using will give you a dropdown box in the printer property page when you have it up and you just drop to the one you wish to use- it may be on your network but you have to point the computer to it.....
this is kinda funny but have heard it said more than once "most of the computer problems are sitting in front of the monitor"....no harm intended.....but have fun with it....it will only do what you tell it to-you just have to know where to go to find out how!
or the program you are using will give you a dropdown box in the printer property page when you have it up and you just drop to the one you wish to use- it may be on your network but you have to point the computer to it.....
this is kinda funny but have heard it said more than once "most of the computer problems are sitting in front of the monitor"....no harm intended.....but have fun with it....it will only do what you tell it to-you just have to know where to go to find out how!
Quick Launch - 101
Just a little tweak tonight for those of you who are messing around with Windows 7 and don't know how to do the basics.....I find the "quick launch" toolbar to be the most helpful as you don't have all those icons all over the desktop covering up your picture/background...to enable quick launch right click on the lower toolbar>go to "toolbars" and tick "quick launch"....easy.....now, for the icons on the desktop that you want to use on quick launch just right click on the icon and hit "pin to taskbar"....easy....then you can delete the desktop icon and it will stay on quick launch...out of the way but useful to you.....to move them around on the quick launch toolbar just left mouse click and hold down and drag it around....where you want it....easy.....even if you go into all the program list you can right click on each program that you want readily available and hit "pin to taskbar" and there it is!
Wireless Adapters....how to install.....
If any of you are using a USB wireless adapter or wireless card internally with Windows 7 DO NOT...I repeat....do not install the driver "software" that comes with it....it seems all the software with these things is buggy.....just let Windows 7 install the basic driver....(you have to be online though so keep your hard wire plugged in till you get it...) then let Windows Zero Configuration run the wireless network for you rather than the software situation.....if you don't...you will run into conflicts....
Keep your life simple....don't load any more software than you can help or you may need help!
Keep your life simple....don't load any more software than you can help or you may need help!
Sunday, May 2, 2010
"Glide" in the Cloud
Well, as we have shown you in prior posts, cloud computing is the way things are headed and are already in full swing. Here is a cool thing for you to check out....your own cloud based operating system you run within your browser window from anywhere you are in the Web World--with 30 GB of free space too!
Check out all the goodies about it HERE
Download it into your Firefox browser HERE
Check out all the goodies about it HERE
Download it into your Firefox browser HERE
Subscribe to:
Comments (Atom)